The Swedish national CERT published a CTF on their website to kick of the cyber security month in the form of a zip-file: CERT-SE_challenge2020.zip
Step 1
Open pcap in Wireshark. Most of the activity is between 192.168.122.156 and 192.168.122.129. Let’s filter by it.
ip.addr == 192.168.122.156 && ip.addr == 192.168.122.129
Chat
tcp.stream eq 7
The interesting parts:
:[email protected] JOIN :#RetroForum
:[email protected] PRIVMSG #RetroForum :Yo!
PRIVMSG #RetroForum :Yo!/Sup?
:[email protected] PRIVMSG #RetroForum :Sup?
PRIVMSG #RetroForum :I was thinking about what you said earlier. I still can't accept that you perfer the Z80?
:[email protected] PRIVMSG #RetroForum :What now??? The Spectrum is waaaaay faster than the C64!!!
PRIVMSG #RetroForum :Sure the CPU, yes. But hardware sprites, a soundship that doesn't sound like a cat beeing strangled, and the possibility for for paralax scrolling?
:[email protected] PRIVMSG #RetroForum :You're just talking about superficial "flair". It's like putting makeup on a pig, it's still slow...
PRIVMSG #RetroForum :Dude you're soooooo wrong!!! Just have a look at the demo I uploaded to the FTP earlier, I'll PM you the password with our usual "encryption".
PRIVMSG Sp3ccyF4n :The code is: "OC1iaXQtQzBtcHV0M2VyLXcwbmQzciE/".
:[email protected] PRIVMSG #RetroForum :Thanks... But I don't think it's relevant. You wont convince me! CPU-power is EVERYTHING. My Z80 is kicking your lazy 6502!!!
PRIVMSG #RetroForum :Whatever... All I have to say is SID6581, nuff said!
:[email protected] PRIVMSG #RetroForum :Like you said... Whatever...
KICK #RetroForum Sp3ccyF4n
:[email protected] KICK #RetroForum Sp3ccyF4n :SID-v1si0uS
A password protected file is shared via FTP. The “encrypted” password is OC1iaXQtQzBtcHV0M2VyLXcwbmQzciE/.
Downloading of file via FTP
tcp.stream eq 9
220 (vsFTPd 3.0.3)
USER sidden
331 Please specify the password.
PASS k3b4bt411rik
230 Login successful.
(...)
STOR demo.tar.xz
150 Ok to send data.
226 Transfer complete.
(...)
The file demo.tar.xz is downloaded from the FTP server. We want that file. Filter by protocol FTP-DATA -> Follow TCP Stream -> Save data as Raw.
Step 2
Decompress the file demo.tar.xz:
$ tar xfv demo.tar.xz
x demo.zip
$ unzip demo.zip
Archive: demo.zip
[demo.zip] cert-se ctf2020.tap password:
password incorrect--reenter:
skipping: cert-se ctf2020.tap incorrect password
The “encryption” of the password is base64:
$ echo -n "OC1iaXQtQzBtcHV0M2VyLXcwbmQzciE/" | base64 -d
8-bit-C0mput3er-w0nd3r!?
% unzip -P '8-bit-C0mput3er-w0nd3r!?' demo.zip
Archive: demo.zip
inflating: cert-se ctf2020.tap
Step 3
The file cert-se ctf2020.tap file and the chat about C64? Let’s fire up a Comodore 64 emulator and load the file as a tape! VICE is free, open source and works on most platforms.
Attatch and autoload the tap file.
Step 4
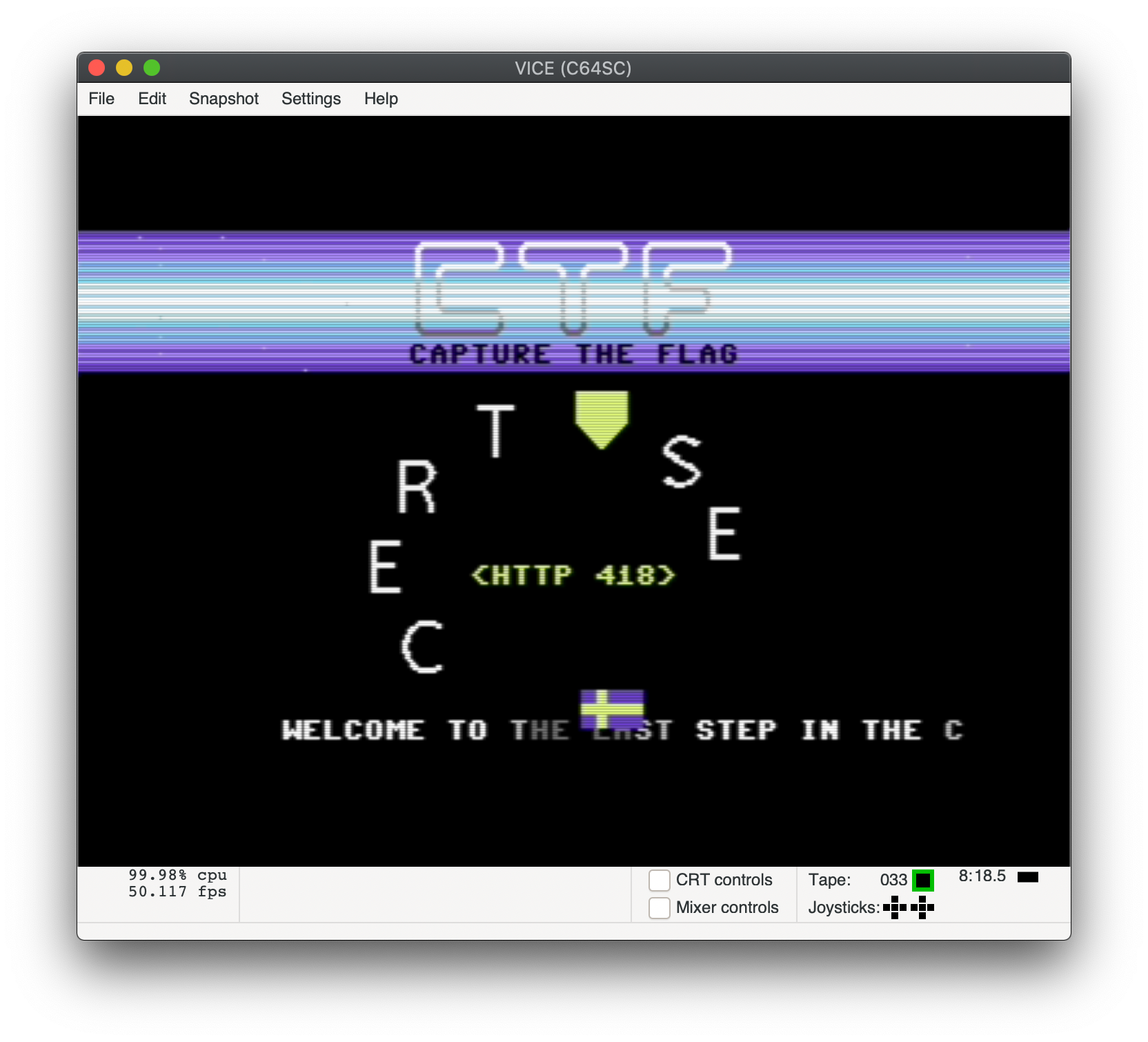
VICE running cert-se ctf2020.tap
This reveals a demo with the text <HTTP 418>in the center and a scrolling text informing us that this is the final step: What does it mean?
The HTTP status code 418 is defined in the Hyper Text Coffee Pot Control Protocol (HTCPCP/1.0) (described in RFC2324, a protocol for controlling, monitoring, and diagnosing coffee pots).
Any attempt to brew coffee with a teapot should result in the error code “418 I’m a teapot”. The resulting entity body MAY be short and stout.
